Spyware's Hidden Dangers: What It Can't Do
In the digital age, our lives are increasingly intertwined with technology, making us vulnerable to unseen threats lurking in the vast expanse of the internet. Among these, spyware stands out as a particularly insidious form of malicious software, designed to infiltrate your computer system without your knowledge or consent. It operates in the shadows, secretly collecting and sending data about your activities, often without your explicit permission. Understanding this stealthy adversary is crucial for safeguarding your digital life, especially given its potential impact on your finances and personal security, making it a significant concern under the "Your Money or Your Life" (YMYL) guidelines.
While spyware is adept at a myriad of covert operations, from tracking your browsing habits to altering your system settings, there's a common misconception about its full capabilities. Many wonder about the precise limits of this digital eavesdropper. This article will delve deep into the world of spyware, exploring what it typically does, and more importantly, address the core question: what are the things that spyware can result in all of the following except?
Table of Contents
- Understanding Spyware: The Invisible Data Collector
- The Common Manifestations of Spyware
- What Spyware Doesn't Typically Do: The "Except" Explained
- Distinguishing Spyware from Other Malware
- The Broader Impact: Why Spyware is a YMYL Concern
- Protecting Yourself: Proactive Measures Against Spyware
- Staying Vigilant: Recognizing the Signs of Infection
- Conclusion
Understanding Spyware: The Invisible Data Collector
At its core, spyware is a type of malicious software designed for covert surveillance. It infiltrates a computer system, often without the user's explicit knowledge or consent, and then secretly collects and transmits data about the user's activities. Think of it as a digital spy, constantly monitoring your actions and reporting back to a third party, typically for nefarious purposes. This data can range from your browsing history and search queries to more sensitive information like login credentials, credit card numbers, and personal communications.
The stealthy nature of spyware makes it particularly dangerous. Unlike ransomware, which announces its presence by locking your files, or traditional viruses that might visibly disrupt your system, spyware often operates silently in the background, making it difficult to detect. It might be bundled with legitimate-looking software downloads, hidden in deceptive email attachments, or installed through vulnerabilities in your browser or operating system. Once installed, it begins its data collection, sending the information to remote servers controlled by the attackers. This clandestine operation is precisely why understanding its capabilities and limitations is paramount for digital security.
The Common Manifestations of Spyware
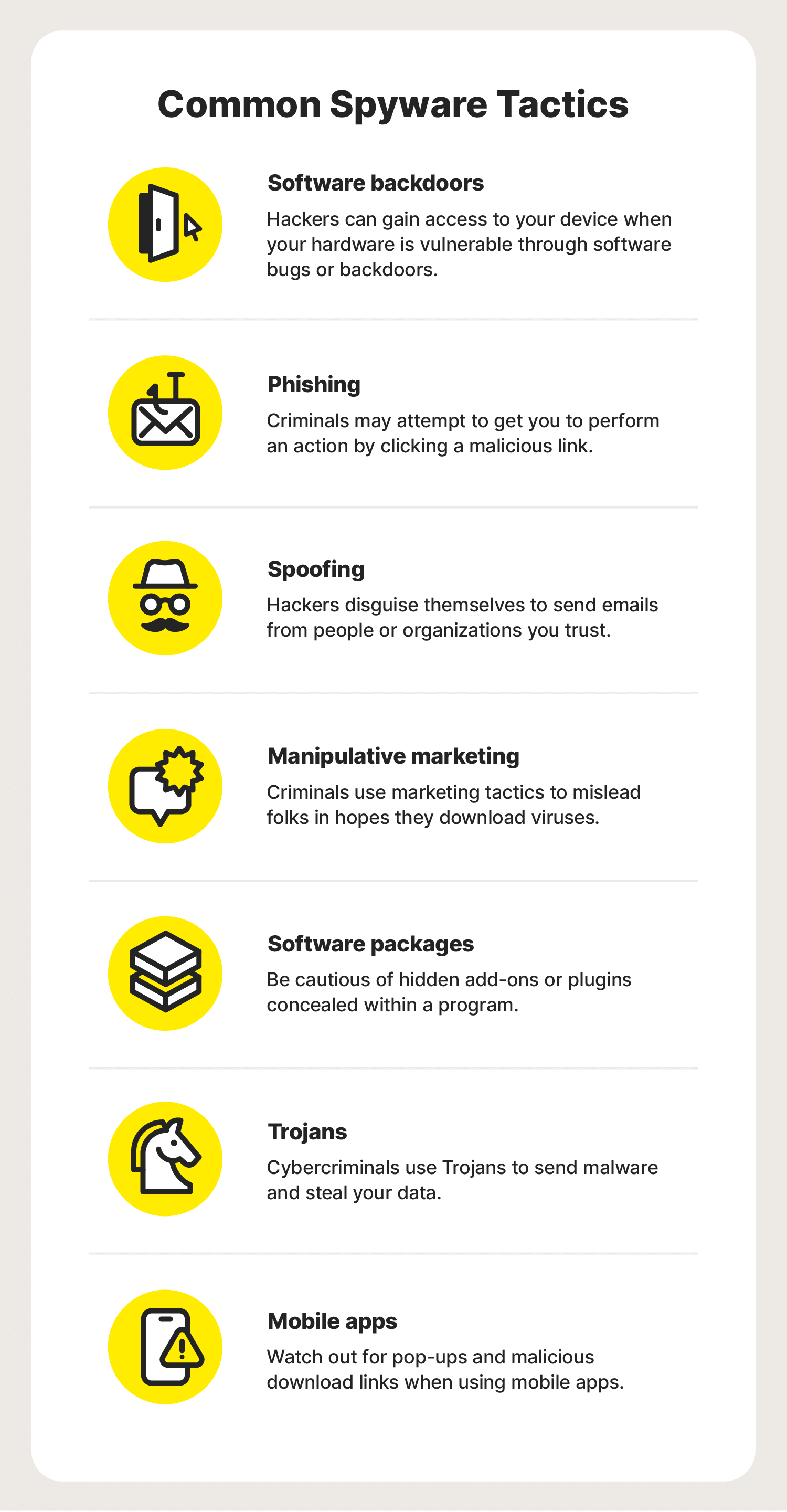
While spyware’s primary goal is data collection, its presence can manifest in various noticeable ways, often leading to a degraded user experience and significant security risks. Recognizing these symptoms is the first step towards mitigating the damage. When considering what spyware can result in all of the following except, it's important to first understand what it *can* and *does* do.
Your Computer's Configuration Changes Without Consent
One of the more frustrating and often immediate signs of a spyware infection is when your computer's configuration changes without your consent. This can involve your browser's homepage being reset to an unfamiliar search engine, new toolbars appearing that you didn't install, or even changes to your default security settings. These alterations are usually designed to redirect your web traffic, display unwanted advertisements (often in conjunction with adware, which we'll discuss later), or make your system more vulnerable to further infections. For instance, a spyware program might change your DNS settings to redirect you to malicious websites, or lower your firewall settings to allow more unauthorized access.
Receiving Emails Soliciting Personal Information
While spyware itself is primarily a data collector and transmitter, its presence can indirectly lead to other security incidents, such as receiving emails that solicit personal information. This often happens because the spyware has collected your email address and other personal details, which are then sold to spammers or phishers. These malicious actors then use this information to craft highly targeted phishing emails, attempting to trick you into revealing even more sensitive data like bank account details, passwords, or social security numbers. The more data spyware collects about you, the more convincing and dangerous these phishing attempts become, directly impacting your financial and personal security, highlighting the YMYL aspect of this threat.
Tracking Users and Gathering Personal Information
This is the quintessential function of spyware. It is designed specifically for tracking users and gathering personal information without their knowledge. This can involve monitoring your keystrokes (keylogging) to capture passwords and credit card numbers, recording your screen activity, capturing screenshots, or even activating your webcam or microphone. It tracks your browsing habits, the websites you visit, the products you view online, and even your geographic location. The data collected is then typically sold to data brokers, used for targeted advertising, or, more nefariously, for identity theft and financial fraud. The sheer volume and sensitivity of the information collected make spyware a profound threat to personal privacy and security.
What Spyware Doesn't Typically Do: The "Except" Explained
Now, let's address the central question: spyware can result in all of the following except what? Based on common understanding and the specific context provided, the most consistent answer for what spyware typically does NOT do is "save duplicate files."
Why is this the case? Spyware's fundamental purpose is to gather information about an individual or an organization without their knowledge and send that information to another entity without the user's consent. Its aim is data exfiltration and surveillance, not data proliferation on the infected device. Creating and saving duplicate files on your computer would be counterproductive to its stealthy mission. Such an action would consume disk space, potentially slow down the system, and most importantly, leave a tangible footprint that could easily be detected by the user or antivirus software. Spyware wants to remain hidden, extracting data quietly, not creating unnecessary copies of existing files.
Therefore, while spyware is incredibly versatile in its data collection and transmission capabilities, its operational logic does not involve generating redundant copies of your files. Its focus is on covertly acquiring and transmitting information, not on managing or duplicating your local data storage.
Distinguishing Spyware from Other Malware
The digital threat landscape is vast, and many types of malicious software share overlapping characteristics. It's crucial to differentiate spyware from other forms of malware to understand its specific modus operandi and to grasp why spyware can result in all of the following except certain actions.
Spyware vs. Adware: The Toolbar Conundrum
One point of confusion often arises regarding new toolbars appearing on your browser. While the provided data suggests that "a new toolbar on your browser that you didn't install is not a spyware symptom," it also states that spyware "can result in various issues, such as... seeing a new toolbar on your browser that you didn't install." This apparent contradiction highlights the close relationship between spyware and adware. Adware, a type of software that automatically displays unwanted advertisements, often comes bundled with spyware or other Potentially Unwanted Programs (PUPs). Both adware and spyware are collectively referred to as "grayware" because they fall into a gray area between legitimate and purely malicious software, often exhibiting intrusive but not always overtly destructive behaviors.
While a new toolbar might be a symptom of *adware* (which itself can collect data for advertising purposes), it's not the primary, direct result of *spyware's* core function of covert data exfiltration. Spyware focuses on data collection; adware focuses on ad delivery. They often coexist or are bundled together, making it hard for users to distinguish the exact culprit behind a specific symptom. However, the act of simply *adding a toolbar* is more characteristic of adware than the stealthy data-gathering nature of pure spyware.
Spyware vs. Control-Oriented Malware
Another important distinction is between spyware and malware designed for direct control over a device. Malware like ransomware, rootkits, or botnet agents aim for overt control: locking your files, gaining deep system access, or turning your computer into a zombie for distributed attacks. Spyware, on the other hand, is generally not designed to take full control over your device in a way that prevents you from using it or holds it hostage. Its objective is covert monitoring and data theft, not system disruption or complete takeover.
For instance, if malicious code is planted on your computer and alters your browser's ability to find web addresses, redirecting you to fraudulent sites, this is known as "pharming." While pharming can be part of a broader attack facilitated by malware, it's a specific type of browser manipulation, distinct from spyware's core data collection. Spyware might gather information that aids in such attacks, but its direct function isn't to flood a computer with data or overtly seize control. Its success lies in its ability to remain undetected while it harvests your sensitive information.
The Broader Impact: Why Spyware is a YMYL Concern
The implications of a spyware infection extend far beyond mere inconvenience. For individuals, the risks are profound and directly align with the "Your Money or Your Life" (YMYL) criteria. The gathering of personal information by spyware can lead to:
- Identity Theft: Stolen personal data like Social Security numbers, dates of birth, and addresses can be used to open fraudulent accounts, obtain loans, or commit crimes in your name.
- Financial Fraud: Captured banking credentials, credit card numbers, and online payment details can result in direct financial losses from unauthorized transactions.
- Reputational Damage: Private communications or sensitive photos collected by spyware could be used for blackmail or public humiliation.
- Loss of Privacy: The feeling of being constantly watched and having your every digital move monitored can be deeply unsettling and erode trust in technology.
For organizations, particularly those handling sensitive data (like government agencies or financial institutions), spyware represents a significant insider threat. While the provided definition of an insider threat refers to a person with legitimate access who misuses it, spyware can effectively turn an employee's compromised device into an unwitting "insider," leaking confidential information. This can lead to massive data breaches, regulatory fines, loss of customer trust, and severe reputational damage. The economic and security ramifications underscore why vigilance against spyware is not just a personal matter but a critical component of national and corporate cybersecurity.
Protecting Yourself: Proactive Measures Against Spyware
Given the pervasive and dangerous nature of spyware, proactive protection is essential. Implementing a multi-layered security strategy can significantly reduce your risk of infection. Here are some key measures:
- Install and Maintain Antivirus/Anti-malware Software: A reputable security suite is your first line of defense. Ensure it includes real-time protection against spyware and is kept updated regularly. Tools like Windows Defender or third-party solutions from trusted vendors (e.g., Bitdefender, Kaspersky, Norton) are crucial.
- Keep All Software Updated: Regularly update your operating system, web browsers, and all applications. Software updates often include patches for security vulnerabilities that spyware might exploit to gain access.
- Practice Cautious Browsing Habits: Be wary of suspicious links, unsolicited pop-up advertisements, and untrusted websites. Avoid downloading software from unofficial sources. As the guidance for government computers suggests, it's wise to "avoid casual or unnecessary internet browsing" on devices that contain sensitive information.
- Use Strong, Unique Passwords and Multi-Factor Authentication (MFA): Even if spyware captures your password, MFA can provide an additional layer of security, making it harder for attackers to access your accounts.
- Be Skeptical of Unsolicited Emails and Downloads: Phishing emails and malicious attachments are common vectors for spyware. Always verify the sender before clicking on links or downloading files. If an offer seems too good to be true, it probably is.
- Employ a Firewall: A firewall monitors incoming and outgoing network traffic, blocking unauthorized access to your computer.
- Use a Virtual Private Network (VPN): A VPN encrypts your internet connection, making it harder for spyware (and other snoopers) to intercept your data, especially on public Wi-Fi networks.
By adopting these practices, you can significantly bolster your defenses against spyware and other forms of cyber threats, safeguarding your personal and financial well-being.
Staying Vigilant: Recognizing the Signs of Infection
Despite your best protective efforts, no system is entirely foolproof. Therefore, knowing how to recognize the signs of a potential spyware infection is crucial for timely intervention. While spyware can result in all of the following except saving duplicate files, it does manifest in other ways that can indicate its presence:
- Slow Performance: Your computer suddenly becomes sluggish, applications take longer to load, or your internet connection slows down significantly. This can happen as spyware consumes system resources and bandwidth to collect and transmit data.
- Frequent Crashes or Freezes: Unexplained system crashes, blue screens of death, or applications freezing could indicate conflicts caused by malicious software.
- Unusual Pop-ups: An increase in unusual advertisements or pop-up windows, even when you're not browsing the internet, can be a sign of adware or spyware.
- New, Unknown Programs: You notice new icons on your desktop, programs in your Start menu, or processes running in Task Manager that you don't recognize and didn't install.
- Increased Network Activity: Your internet usage spikes unexpectedly, even when you're not actively using the internet, indicating data being sent from your computer.
- Browser Changes: Your browser's homepage, default search engine, or other settings are altered without your permission, or you're redirected to unfamiliar websites.
- Security Software Disabled: Your antivirus or firewall software is mysteriously turned off or unable to update.
If you observe any of these symptoms, it's imperative to take immediate action. Run a full system scan with your updated antivirus/anti-malware software. If necessary, seek assistance from a cybersecurity professional. Early detection and removal are key to minimizing the damage spyware can inflict.
Conclusion
Spyware represents a significant and evolving threat in our interconnected world, silently compromising our privacy and jeopardizing our financial security. It is a sophisticated form of malicious software designed to collect and transmit sensitive personal information without your knowledge or consent. From tracking your online activities and altering system configurations to potentially exposing you to phishing attempts, its capabilities are extensive and deeply concerning, especially given the YMYL implications for individuals and organizations.
However, it is vital to remember the specific limitations of this digital intruder. While it excels at covert surveillance and data exfiltration, spyware can result in all of the following except one key action: saving duplicate files. This distinction helps us understand its true nature as a data collector, not a file duplicator. By understanding its true functions and the ways it differs from other malware, we can better protect ourselves.
Staying vigilant, employing robust cybersecurity practices, and being aware of the signs of infection are your best defenses. In an era where personal data is a valuable commodity, protecting your digital footprint is not just a technical task, but a crucial aspect of safeguarding your life and livelihood. Share this article to help others understand the nuances of spyware, and feel free to leave a comment below with your thoughts or experiences. For more insights into digital security, explore our other articles on cybersecurity best practices.

The Spyware - Telsy
types of spyware Spyware common types detect them - Anime Manga Drawing
Spyware: What it is and how to protect yourself - Norton